
Cybersecurity Insights from Our 'Resilience by Design' Seminar
Cyber threats are evolving fast, and so must our defenses. At our recent security seminar, Resilience by Design, we explored the latest trends, legal nuances, and best practices to help organizations like yours stay ahead. Here’s a quick recap of what you need to know.
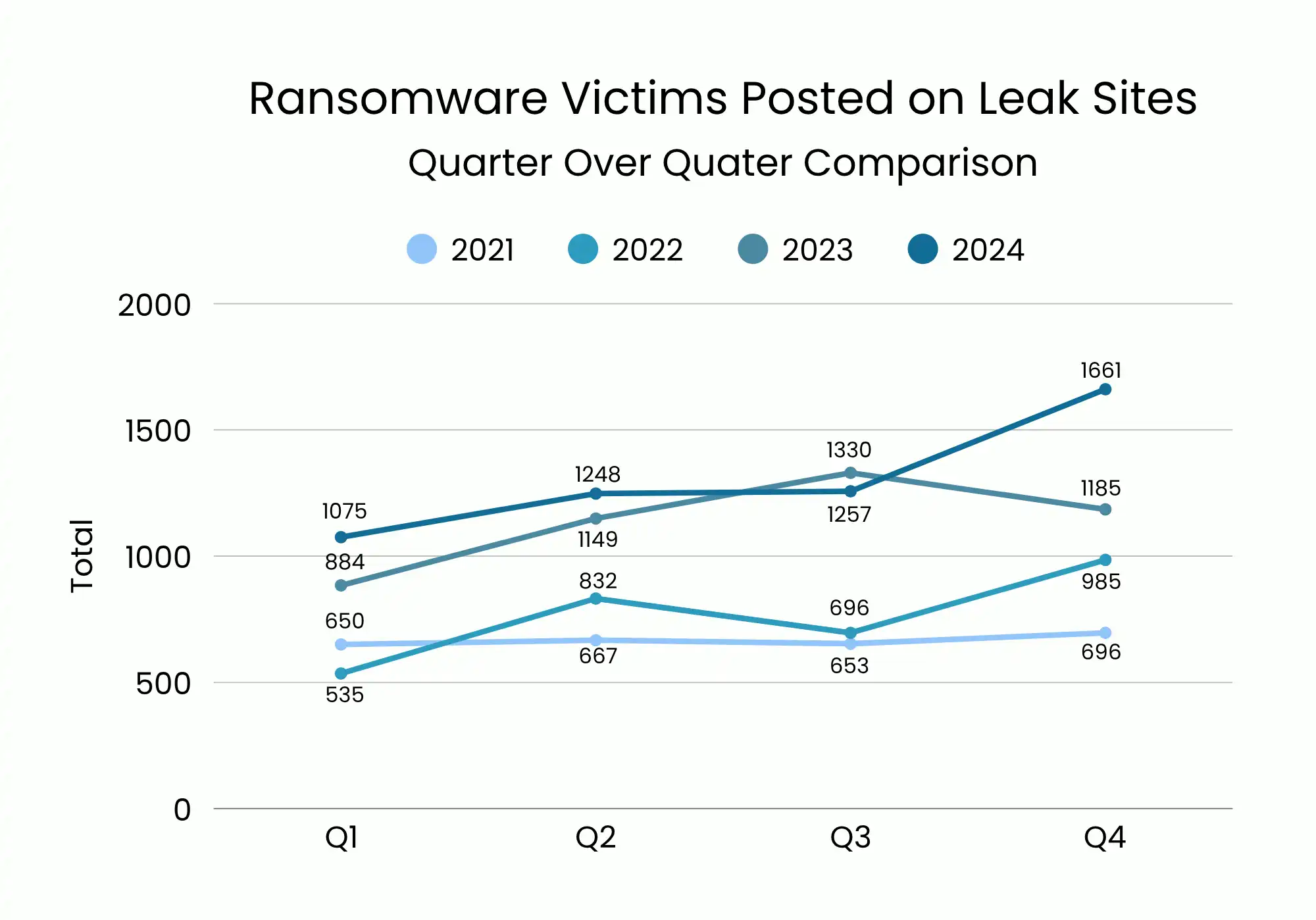
The State of Cybersecurity
- Ransomware is rampant: 53% of cyber insurance claims stem from ransomware, and some payouts reach $50 million.
- Attackers don't hack in – they log in: 77% of web app attacks start with stolen credentials.
- Password reuse is rampant: 85% of users reuse passwords.
- Account takeovers: 83% of organizations experienced at least one.
- Business Email Compromise (BEC) is on the rise: 56% of BEC claims occurred in just the last three years.
- In 2024, ransomware attacks hit 5,243 victims – a 15% increase from 2023.
- Globally, these attacks exposed 195+ million records and cost $813 million in ransom payments
- Average downtime after a cyber incident? 22 days.
Don’t Say the “B” Word (Yet)
Calling an incident a “breach” too early can trigger legal and regulatory consequences. Here is the breakdown:
- Security Event: Suspicious activity like phishing or firewall alerts
- Security Incident: Confirmed threats like malware or insider misuse.
- Breach: Unauthorized access to sensitive data – only your legal team should make this call.
What Counts as an Incident?
An incident can include ransomware attacks, email compromise, wire fraud, insider threats, or accidental data exposure.
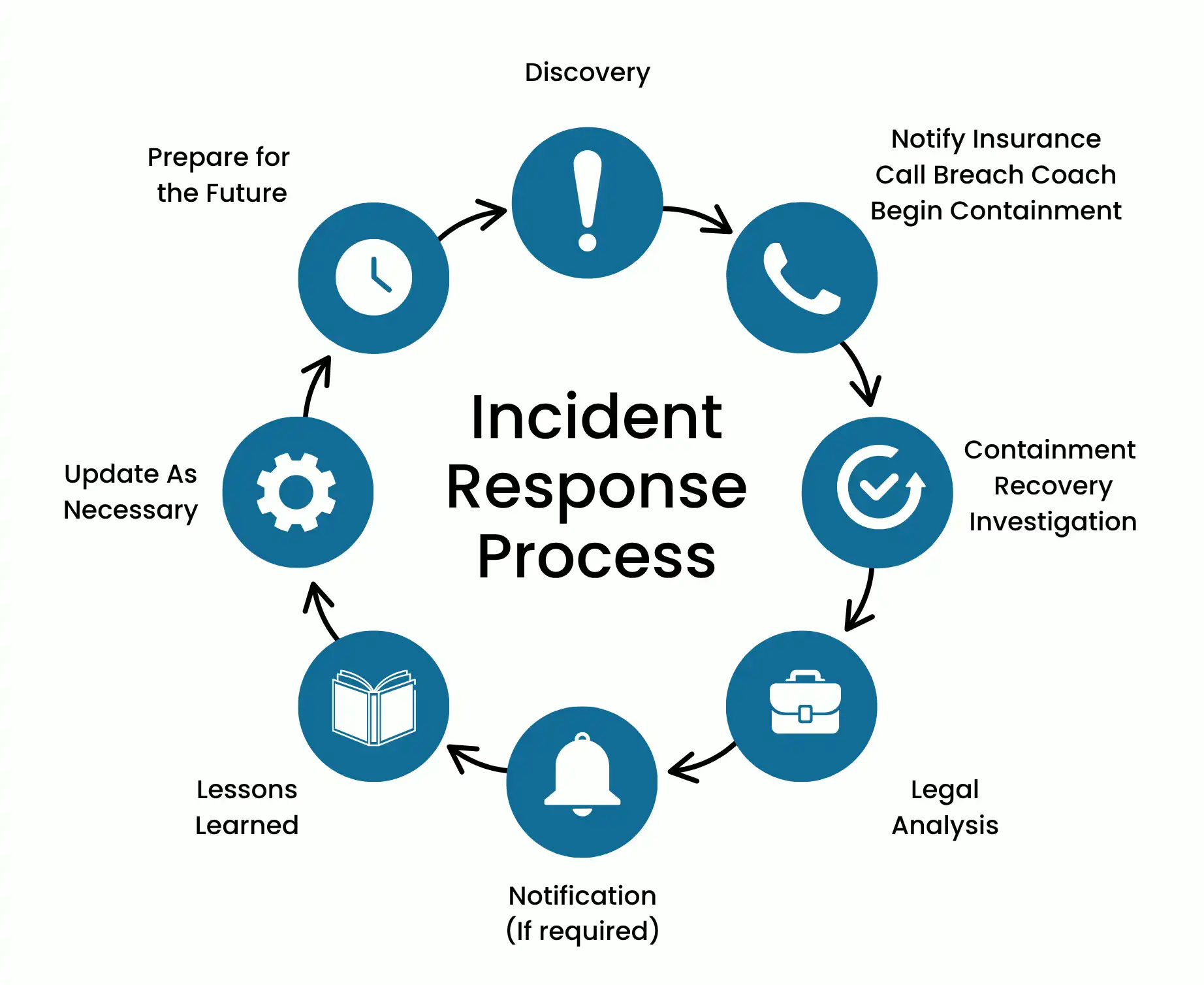
Who’s on Your Incident Response Team?
Your incident response team should include IT leadership (such as the CIO or CTO), executive leadership (like the CEO or CFO), human resources, legal counsel (often referred to as your “breach coach”), forensics experts, and your cyber insurer.
Best Practices
Pre-Breach
Have a plan: Create a Written Information Security Plan (WISP) and Incident Response Plan. This plan should include:
- Preparation: Define roles, communication paths, and external contacts.
- Detection: Use SIEM/XDR tools, AI, and behavior analytics
- Containment: Isolate systems, change passwords, stop lateral movement.
- Eradication & Recovery: Remove malware, patch systems, restore clean backups.
- Post-Incident Review: Learn from the event and update your policies.
Practice: Run tabletop exercises with legal and security teams.
Minimize data: Don’t collect what you don’t need
Limit access: Only those who need data should have it.
Train employees: Awareness is your first line of defense
Vet vendors: Ensure they follow strong security protocols and include protective clauses in contracts.
Post-Breach Response
- Follow your Incident Response Plan
- Mitigate harm quickly
- Notify your insurer and legal team
- Work with forensic experts under the attorney-client privilege
Cyber Insurance Tips
To qualify for cyber insurance coverage, many insurers now require organizations to implement key security measures such as multi-factor authentication (MFA), encrypted and segmented backups, timely software patching, endpoint detection tools, and a well-documented cybersecurity program. It’s also critical to submit honest and thorough insurance applications, as incomplete or inaccurate information can jeopardize your coverage when you need it most.
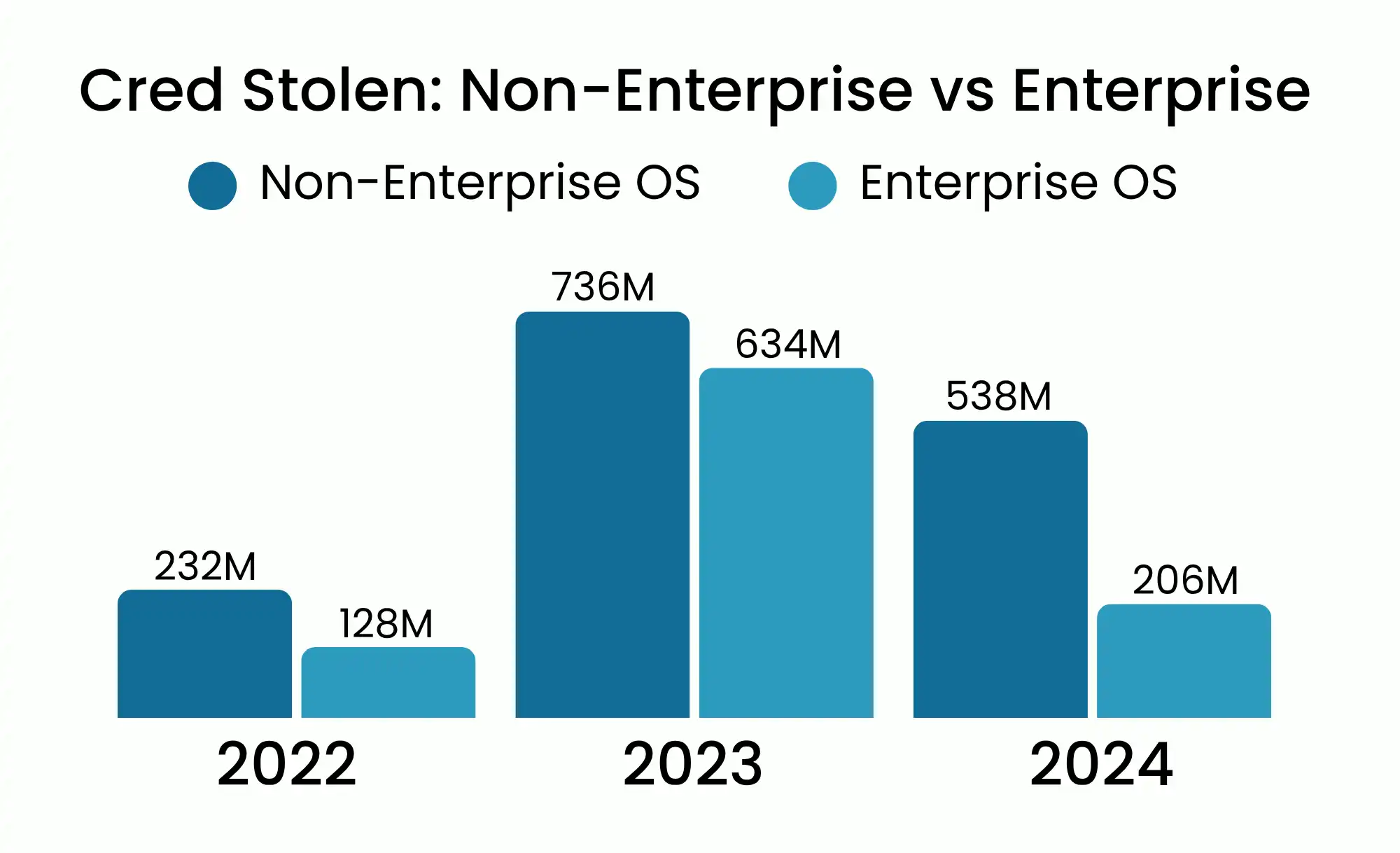
Criminals Gain Enterprise Access From Personal Devices
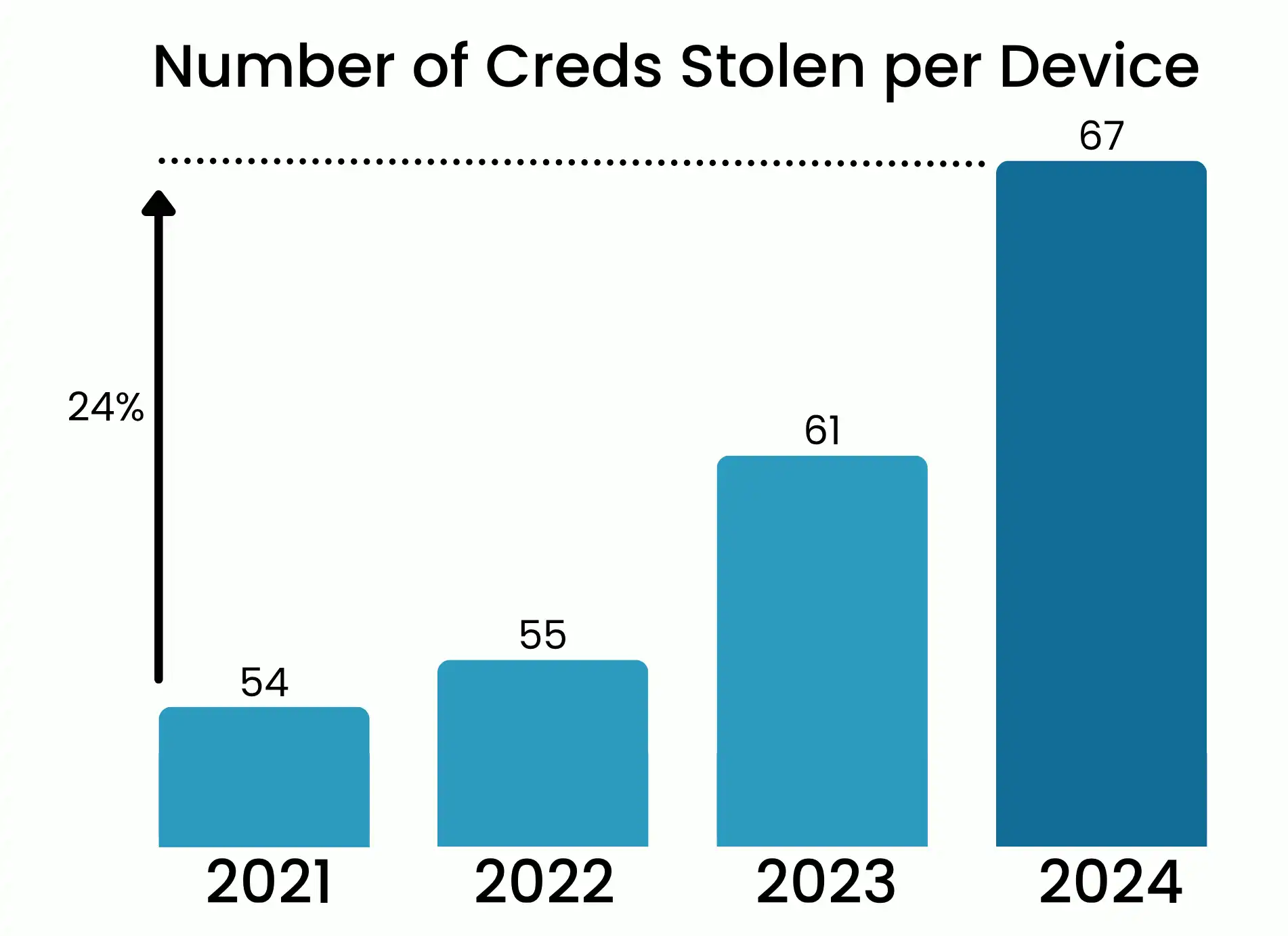
Common Pitfalls
When it comes to managing security incidents, several common pitfalls can seriously hinder an effective response. Unclear roles often lead to confusion during critical moments, while poor communication can delay action and escalate the impact. Without documented procedures, teams may struggle to know what steps to take, and a lack of training leaves staff unprepared for real-world threats. Over-reliance on tools can create a false sense of security, and ignoring lessons from past incidents means missing valuable opportunities to improve. Addressing these gaps is essential for building a resilient and responsive incident management strategy.
2025 Outlook: What’s Ahead
Cyber threats aren’t slowing down – and neither should we. Staying informed, prepared, and proactive is the key to resilience. In our next blog, we’ll dive into “Securing the Future: Cyber Security in 2025 with EDCi and Microsoft” – exploring the latest tools, trends, and technologies shaping the next generation of digital defense. Stay tuned!
Special thanks to Sarah Sargent, Privacy & Cybersecurity Attorney at Godfrey & Kahn, and to Andy Sokol and Zach Kaiser from McClone Insurance for sharing their expertise at our recent event. For specific guidance related to your legal or insurance needs, we recommend consulting directly with the qualified professionals listed above. EDCi is dedicated to helping organizations thrive through innovative technology solutions. Connect with us today to learn how we can support your incident management strategy and strengthen your organization’s security for the future.



